- Disable User
- Posts
- The aCROPalypse is neigh and Brazil bans pentesting tool.
The aCROPalypse is neigh and Brazil bans pentesting tool.
Security weekly

Hi and welcome to another Security weekly. Where we laugh, we cry and share the latest and greatest in security and tech news.
In this week's edition:
🪖aCROPalypse Now - privacy flaws in Windows Snipping Tool
👔 Fashionable tools for hackers
❔Disable User Explains: Pentesting
🔥 the quick and dirty
Reading time: 03:37

Acropalypse Now - privacy flaws in Windows Snipping Tool
Good news and bad news. (number one thing you don’t want to hear after plastic surgery)
The good news
The bad news isn’t as bad as the events in the Coppola movie, Apocalypse Now.
The bad news
My trusty companion, the Windows Snipping Tool, has a severe privacy flaw.
Not only the Windows Snipping tool, but also Google Pixel’s Markup tool.
Last week it was uncovered that, when editing or blurring a picture, the original data is still maintained.
Making it possible to (partially) recover the original content.
That’s like playing hide & seek with my kid

Anybody know where he is?
So, how is this all possible?
A PNG, like any file, is made from bytes. The PNG file type specifies that every range of bytes is ended by IEND.
This way the PNG file knows when to stop looking, and can build the image.
The weird thing is, if you edit the picture with the Snipping Tool and save it, the size remains unchanged.
You’d expect a smaller - cropped - image to be smaller, right?
This odd finding triggered vulnerability expert Will Dormann to take a deeper look what exactly happened to the data, who later published his findings.
To make this a little more understandable, ya boy took it upon him to demo this and make it more understandable through screenshots.
Talking about bits and bytes is boring enough as it is.
Hope you appreciate the effort.
I mean, I really put in effort.
(I took 2 screenshots, cropped one, mistakenly deleted the wrong one, opened the editor again, clueless why it didn’t work, until I realized what I did.)
But, here’s the demo;
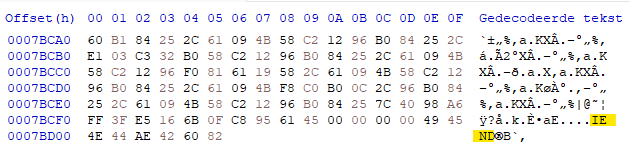
A PNG I opened with a hex editor, confirming it ends with IEND.
I then cropped the above file and saved it over the original file.
After taking another look with a hex editor something peculiar shows up.
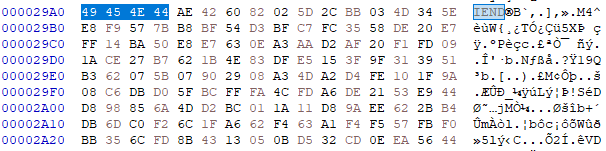
Data behind the IEND?
The original bytes of the part that is left out of the cropped version is still stored in the file, it’s just not shown.
A PNG doesn’t read behind the IEND, so it only shows the bytes before my cropped picture, but the original information remains there.
Making it obtainable for others.
So, think twice next time you share a picture with “blurred” information you really don’t want people to know.

Get it? It’s cropped. aCROPalypse.. ah nvm.

Fashionable tools for hackers
Last week the Brazilian government made a rather weird statement by banning Flipper Zero devices.
For those unaware, Flipper Zero is a popular pocket-sized tool for pentesters and geeks alike.
With many emulation features like radio frequencies, NFC, IO possibilities lot’s of other stuff.

Look at the cute dolphin
Because the tool could be used with malicious intent, the Brazilian government revoked it’s license, making it illegal.
But that’s like saying all steak knives should be banned because I could use it to shank someone.
In 99,9% of the cases, steak knives are used to … cut steak.
Except when I’m hangry, got to be careful then.

Exceptions apply
Anyway..
Penetration testing (pentesting) is truly vital for any company who takes security seriously.
Cloud environments, servers, everything online but let’s not forget card access systems and any physical controls we have in place.
And that’s where Flipper Zero comes in handy.
So by banning that cute dolphin, you’re doing more harm than good. You’re stopping the good guys, and bad guys don’t care about any bans.
So, to make it easier for the Brazilian government to make a good decision next time, here’s a list of tools used for hacking that should not be banned:
Angry IP Scanner - this IP scanner is ANGRRYYY. And also very useful. Gives a quick layout for any network you’re connected to.
Mimikatz - easy to use tool that can extract plain text passwords, hashes, pin codes and Kerberos tickets from memory. Scary to watch.
Kali Linux - the OS made for pentesting. Wouldn’t recommend if you don’t know what you’re doing.
Metasploit - more a vulnerability framework than one single tool. Includes a lot of useful stuff for pentesting. Also comes pre-installed on Kali.
Wireshark - the GOAT packet sniffer. Every IT’er who’s done anything with networking or packets in particular knows about Wireshark. Easy to use, hard to master.
Lockbit - just kidding, that’s some evil hacking software right there. If you’ve followed the newsletter for a bit you should already know that.

Penetration testing (pentesting)
The art of simulating a cyberattack on computer systems to surface vulnerabilities and weaknesses.
Doable on anything cyber related;
Websites, webshops
Public, private, hybrid cloud environments
Infrastructure
Applications
…
I’d advice any company to perform at least one per year on the platform you think necessary.


The quick and dirty
Mozilla Firefox 111.0.1 fixes Windows 11 and macOS crashes - quite annoying, glad it’s fixed.
Ferrari discloses data breach after receiving ransom demand - they didn’t pay, it’s only customer data after all..
How to keep your Twitter secure without giving Elon Musk any money - funny how much lengths people go through to talk about Elon.
New York Man Arrested for Running BreachForums Cybercrime Website - not saying Breached was good, but it was a handy source to check for leaked info.
Meme of the week

