- Disable User
- Posts
- 👁️ I can see inside your Microsoft 365 tenant
👁️ I can see inside your Microsoft 365 tenant
and this week's Bits & Bytes

Hi and welcome to another Security weekly. Where we laugh, we cry and share the latest and greatest in security and tech news.
In this week's edition:
👁️ I can see inside your Microsoft 365 tenant
📰 Bits & Bytes
❓ Disable User explains: OSINT
🔥 meme of the week
Reading time: 02:52

I can see inside your Microsoft 365 tenant
Good, now that I have y’all attention.
STORYTIME!

Last week I was called in for an Adversary-in-the-middle attack.
An attack where somebody gets - you’ll never guess what comes next - in the middle of 2 parties.
From that middle, they can then interrupt communication or take over entirely.
This case got my interest and I spent way too much time investigation when, how and what happened.
*record scratch*
*freeze frame*
I’m by no means an ethical hacker, a pen tester or a cybersecurity analyst.
I’m;
fairly good at risk management
good at overseeing situations and how they played out
like to laugh at my own jokes, harder than anyone else
*continue*
In the pursuit of that quest, I came to know a lot about the hackers through OSINT.
Way more than I’ve imagined I would have.
How did I obtain this info?
I had a fake domain they used for typo-squatting
I looked up their DNS records - nothing
Checked their WHOIS info for something - redacted, shame
I checked if they had Microsoft 365 - DING DING DING, BINGO
I used a tool by a colleague, which reverse matches your domain to see if there’s a Microsoft 365 environment attached.
If there is, it shows the tenant id and lists all domains in the environment.
The tool
Give this guy a follow on LinkedIn, he does cool stuff!
I doubt a lot of people know this is possibly.
And it also makes me wonder how many companies will feel exposed, showing their side domains to the world.
The output
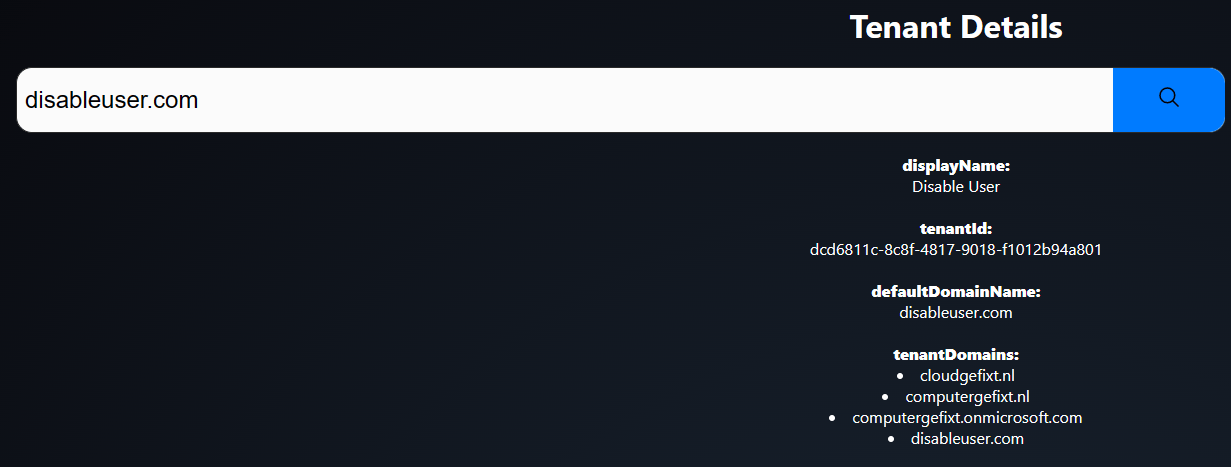
For obvious reasons I won’t use the hacker’s domains.
When I did this for the hacker’s domain, I got a long list of all kinds of typo-squatted domains.
So I did what any sane man would do: check them all by hand.
is there a website?
is their WHOIS hidden?
Which led me to the next step: I found a WHOIS that wasn’t hidden and I even found a functional website.
After some digging around, I found an address, a name,.. I really hit the jackpot.
I still can’t believe hackers would use Microsoft 365, so I’m afraid the person who I found isn’t a hacker but a victim.
What will I be doing with this information?
After informing the affected parties, I’ll take this to Microsoft and probably even authorities.
Since the WHOIS pointed to the United States, I guess that’s the FBI.
I have to admit, reporting something to the FBI scares me.
As a European, the FBI doesn’t really have the reputation of taking things.. easy?

Anyone got any tips or advise on the matter?

Bits & Bytes
Exclusive: Pentagon Investigates ‘Critical Compromise’ Of Air Force Communications Systems - I said I was scared about contacting the FBI. Imagine being this guy.
Apple rejects new name 'X' for Twitter iOS app because... rules - this whole rebranding of Twitter.. are we in a movie plot?
New Android Malware CherryBlos Utilizing OCR to Steal Sensitive Data - be careful what you install - or click. Somebody might be watching.
CISA: New Submarine malware found on hacked Barracuda ESG appliances - Barracuda offered to replace all affected devices last month. If you haven’t done so: apply now.
CVE-2023-35081 - New Ivanti EPMM Vulnerability - one more in the everlasting line of vulnerabilities. If you’re using Ivanti - you know what to do. It’s rated 10/10, so no lightweight baby
Apple Sets New Rules for Developers to Prevent Fingerprinting and Data Misuse - Apple narrowing down on their API accessibility. Everyone liked that.

OSINT
Open-Source Intelligence: Information that is publicly available and legally accessible.
Examples about this are all around.
Things you can find on websites, LinkedIn or tools like the one I mentioned earlier.
So, businesses owners, be careful what you put online.


Meme of the week