- Disable User
- Posts
- DDoS explained using only toilet references, and a lot of Zero Day action for Apple and Microsoft!
DDoS explained using only toilet references, and a lot of Zero Day action for Apple and Microsoft!
Security weekly

Hi and welcome to another Security weekly. Where we laugh, we cry and share the latest and greatest in security and tech news.
In this week's edition:
🚽 Largest DDoS to date stopped by Cloudflare
☔ It’s raining zero-days
❔ Disable User Explains: Denial of Service attacks
🔥 the quick and dirty
Reading time: 02:47

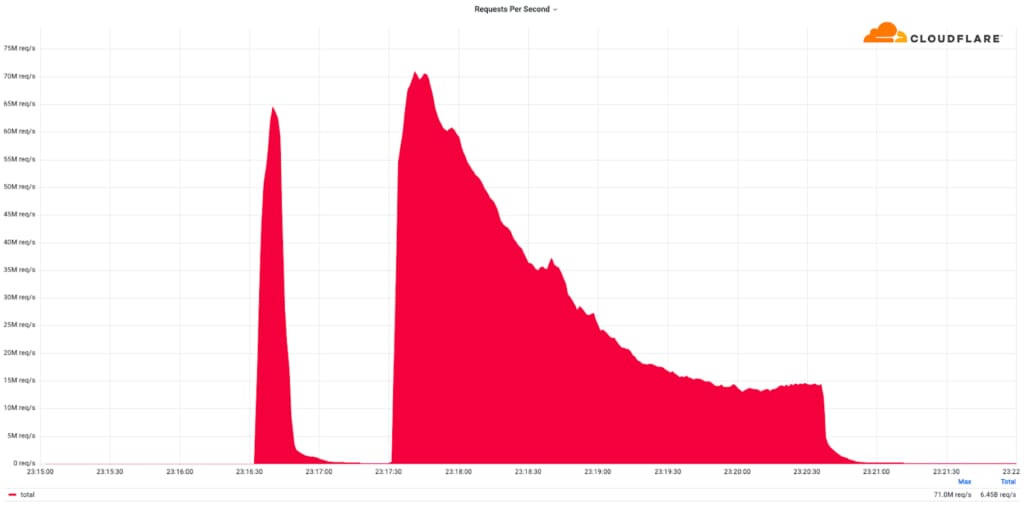
Largest DDoS to date stopped by Cloudflare

Imagine you’re in a public place and you have to go to the toilet. You feel a number 2 coming up. There’s 5 stalls.
As you make your way to one of those stalls, you’re passed by people rushing to those 5 stalls.
“Hm I sure hope there is an empty stall left”, you’re thinking.
As you’re almost there, people keep rushing past you, making it almost impossible for you to move forward.
When you finally arrive, you find out all stalls are taken.
Even worse, there’s a queue of about 71 million people before you. Nobody can get in, or out.
That’s exactly what a Distributed Denial of Service attack is. It’s only intent is to clog traffic and take up all spaces, making it impossible for anything to go in or out and eventually the target will have go down.
To stay in my toilet metaphor; as people continue to queue, toilet paper runs out, pipes get clogged, the WC will become unusable.
So what can you do?
The first thing that comes to mind is; get more toilets? But then again, building 71 million toilets is impossible.
Stand in front of your toilets and try to manage access? Sounds good, but how are you going to stop all those people?
Hire a team of expert crowd controllers? Ding ding ding, we’ve got a winner.
And that’s exactly what Cloudflare does. They specialize in content delivery and DDoS mitigation.
Helping companies fight off 71 million people who all want to clog up your toilets.
If you’re wondering what that looks like;
Did I just write an entire segment using only toilet references? Yes I did.
Some* call me the Shakespeare of my time.
*people with very low standards


It’s raining zero-day exploits
Quite a busy week for sysadmins once more.
First Apple released an update for a Zero-day Webkit vulnerability that was actively exploited ‘in the wild’.
freeze frame
Who are security people kidding when they use “in the wild”? Trying to make is sound way cooler than it actually is.
We’re just nerds sitting behind a computer, people! We’re not hunting lions.

Security people reading this
continue
Only to be topped off by Microsoft a few days later, on Patch Tuesday, who released 77 updates to flaws, and 3 zero-days.

Microsoft hearing Apple just released a critical update.
Other vendors such as Adobe, Atlassian, Cisco and many more also decided to join the party and released loads of security updates.
You can find the full list below in the Quick Bites segment.

Denial of Service
Ok fine, I’ll explain it without toilets as well. *boring*
A malicious attempt to disrupt the availability of a server, service or network by overwhelming the target.
The four most used and known type of DoS attacks:
Application layer flood - the attacker tries to flood the target with many connections from one client.
Distributed denial of Service (DDoS) - the attacker tries to flood the target with connections from many different clients instead of one.
SYN Flood - Same as the other two, but the connection is never finished. The attacker just sends out many requests which use up the target resources.
Ping of Death - the attacker sends just one packet which the target cannot process and therefor crashes. Mostly done by sending oversized packets.


The quick and dirty
Microsoft: Exchange Server 2013 reaches end of support in April - it’s getting close!
French law to report cyberincidents within 3 days to become effective soon - French Law hardening on Cybersecurity or insurance companies leveraging the government..?
Update Now: Microsoft Releases Patches for 3 Actively Exploited Windows Vulnerabilities - Includes full list of all vendors with security updates.
Reddit Suffers Security Breach Exposing Internal Documents and Source Code - Reddit claims no user data was breached, but call me suspicious..
Meme of the week

by Bright Security
