- Disable User
- Posts
- Google goes Passkeys, farewell passwords
Google goes Passkeys, farewell passwords
Cracking the code: cryptography

Hi and welcome to another Security weekly. Where we laugh, we cry and share the latest and greatest in security and tech news.
In this week's edition:
👋 Google goes Passkeys, farewell passwords
🔐 Cracking the code: cryptography
❓ Disable User explains: Shoulder Surfing
🔥 the quick and dirty
Reading time: 03:45

Google goes Passkeys, farewell passwords
BEFORE I HAVE 200 APPLE LOVERS FLOODING MY MAIL:
I know, Apple’s Keychain has similar functionality.

And, for my more geeky readers, some hardware tokens like Yubikeys have had this functionality for a while, though a bit different.
Ok, now that we have that out of the way. What the fuark is a Passkey?
Passkeys are a type of login credential that removes the need to enter a password, or a username for that matter.
It is linked to your biometric or other device login, and uses that to validate you.
It relies on the knowledge that if you can open your device, you’re good to go.
So, Google and Apple went bonkers over the past few months and got it working.
But what’s so great about it?
No more username and password - kinda speaks for itself, but what a relief that will be
Multi device - Create a Passkey from your iPhone/Android once and use it on your Mac/Chrome devices through cloud sync.
Say goodbye to phishing attacks - without a logon action, there’s no more phishing
Did I say it removes the need for a password and username?
Is it all sunshine and rainbows? No, definitely not.
While I said it’s goodbye to phishing, a whole array of other attacks are lurking just around the corner.
Not to forget, your mobile device will be a very wanted target.
If you’re looking for a how-to, Google’s made it pretty easy.

Cracking the code: cryptography
So I asked, and y’all answered. In my last poll I asked what topic you’d like to see, and the answer was clear:
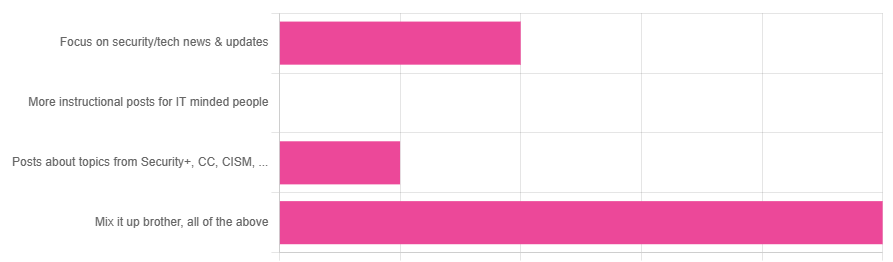
So, LETS MIX IT UUUUPPPP.
On weeks where the news is kind of slow, I’ll do my best to get you enlightened on other topics.
So today, starting with the security GOAT: Cryptography.
I promise to keep things light and fun, and I’ll spread ‘em over the course of a few weeks.

Look at at like this
Cryptography is like a digital masquerade ball.
Your data wears a dazzling mask.
Only those with the secret key can see its true face.
Poetic.
This week’s sub-topic: Encryption
Symmetric Encryption: One Key Does the Trick
In symmetric encryption, we use the same key to lock (encrypt) and unlock (decrypt) our secret messages. Imagine you and your friend have a special box with one key. You can lock your secret note inside and pass the box to your friend.
Your friend can then unlock the box using the same key to read your note.
Real-life use - Protecting your WiFi password or keeping secret files on your computer
Popular algorithms - AES, DES, and 3DES
Meet the symmetric encryption methods:
AES: A strong and widely used choice that keeps your data secure.
DES: An older method, but not very strong now. It's like an old lock.
3DES: A better version of DES, but still not as strong as AES.

When you see DES being used
Asymmetric Encryption: Two Keys to Keep It Safe
Asymmetric encryption uses two keys: a public key and a private key. You can share the public key with everyone, like giving out your email address. The private key is secret, like a password only you know.
Imagine you want to send your friend a secret message. You can lock your message using your friend's public key. The cool part is that only your friend's private key can unlock it!
Real-life use - Sending secure emails or signing digital documents
Popular algorithms - RSA, ECC, and ElGamal
Explore the asymmetric encryption methods:
RSA: A strong and popular option that ensures your data's safety.
ECC: A newer and faster method, but not as well-known as RSA.
ElGamal: A secure but less popular choice.
Symmetric vs. Asymmetric: When to Use Each
Symmetric encryption is fast and great for protecting lots of data, like your secret diary. Asymmetric encryption is slower but perfect for sending secure messages to your friends, like special invites to your clubhouse.
Remember: Both types of encryption are essential for keeping information safe!
Examples and Use Cases
Online shopping - When you buy something online, asymmetric encryption keeps your payment details secure.
Secret chats - Symmetric encryption can be used to keep your private group chat messages hidden.
Digital signatures - Asymmetric encryption helps ensure the documents you sign online are safe and verified.
That's our “fun” and informative journey through symmetric and asymmetric encryption!
I hope next time you’re shining with all that new knowledge, you’ll think of me.
Stay tuned for more exciting discoveries in the world of cryptography, guys & girls!

Shoulder Surfing
Watching someone when they enter their username, password, or sensitive data.
Disclaimer: there’s no actual surfing involved.


The quick and dirty
T-Mobile discloses second data breach since the start of 2023 - “the carrier has disclosed 7 breaches since 2018”. While the whole world is gearing up against cyber threats, T-Mobile goes golfing.
Hackers leak images to taunt Western Digital's cyberattack response - that’s a big OOF, taunting WD like that.
Hackers are increasingly using ChatGPT lures to spread malware on Facebook - who would have guessed, right?
Meme of the week