- Disable User
- Posts
- Hackers and their hats, who's who?
Hackers and their hats, who's who?
Security like I'm five

Hacker(s), a term that has so much and so little to add in any conversation. Most people know the term from movies.Some pale kid who can access any computer system in seconds and calls everything 'the mainframe'.
But what are their intentions? How do you distinguish them?To keeps things clear, categories were invented. Well, hats.
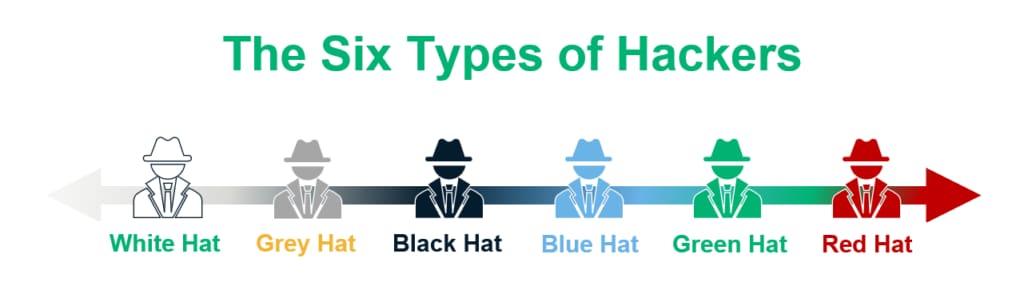
By SectigoStoreEvery hat has their intentions and motivation, but sometimes it's hard to know who's who.Sit tight, grab a drink, and I'm going to tell you all about it in this Security like I'm five.
Security like I'm five: Hackers and their hats
In this post
➡ Defining the hacker➡ So who's who?
reading time: 03:12

Defining the hacker
According to merriam-webster:
"one that hacks"
Well that's not going to get us very far now is it, Merriam?
According to Cambridge dictionary:
hacker~noun [ C ]~UK /ˈhæk.ər/ US /ˈhæk.ɚ/
(also computer hacker)
"someone who gets into other people's computer systems without permission in order to find out information or to do something illegal"
That pretty much covers it, although there is one part of this that isn't necessarily true:~without permission
As I said, most people know the term hackers from movies. Movies where they don't necessarily portrait the good guy.In the real world though, there are good and bad hackers a like. The good hackers have - or ask for - permission.
In my quest for hacker movies I did find this gem called 'El H@cker', which I had to share.Sadly, with an IMDB rating of 4.3, I'll think I'll pass.

If I ever did get into hacking, I want people to call me El Hacker.

So who's who?
White Hat - the good guy
Also referred to as "the ethical hacker".Does penetration testing, takes a look at your vulnerabilities and all with your consent.That last part is very important. Because the further away we go from the white hat, the less permission or consent is requested.

White hat hackers are often in employment, and are constantly on the look-out for new ways to target your environment.Blue and Red hat hackers also fall under the White hat category.
Where Blue hats are hired by company's to sniff out bugs and vulnerabilities in a calm matter, without breaking things. Red hats often try to counter attacks from Black hats, and destroy the attackers systems.
Black hat - the movie villain
The real criminals. Will use any means necessary to steal your data, get into your network and corrupt your systems.In movies they are portrayed as powerful villains, but this is not entirely true. Some examples of Black hats:
Lazarus Group - a North Korean hacker collective mostly known for deploying ransomware to targets that offend their country, or are otherwise interesting for North Korea.
The 19 year old kid who hacked Uber earlier this year - Doesn't sound like a movie villain right? He did know what he was doing though, and is part of a hacker group.
Grey Hat - the mostly good guy
In contradiction to the White hats, Grey hat hackers don't necessarily abide the law. They perform both White and Black hat activity (hence the color grey), but they will still tell you about it after they hacked your system, and will tell you how they did it. "hack first, ask questions later."
Other ideologies for Grey hats might come under the name "hacktivism". Anonymous is a well known example of this.

While some may argue if they're not really Black hats, their cause is just: bring attention to problems in the world.
Green Hat - the up & coming
Not necessarily good or bad yet, but just inexperienced. Their lack of experience can cause a lot of damage, also to themselves.
The difference between Green hats and script kiddies, is that Green hats are looking to upgrade their skills and become worthy White or Black hats.
Bonus - Script kiddie
My 12 years old neighbor, Josh, who just bought a malware tool on the darkweb for $800 and is looking to f some sh*t up - He probably won't do much damage. But he is on the wrong side of the law when he sends out 10k phishing mails in an attempt to steal personal information.


While there may be some other colors and hats sometimes used, I think this is plenty.It's good to know who's who, but I think their intentions will most likely be clear rather quick.
I hope this post helped shed a light on all types of hackers. As always:stay safe and when in doubt: Disable User!
