- Disable User
- Posts
- SecPro turns Karen
SecPro turns Karen
Security weekly

Hi and welcome to another Security weekly. Where we laugh, we cry and share the latest and greatest in security and tech news.
The Rubik's Cube has 43 252 003 274 489 856 000 possible combinations. That's still one less than the recommended password length recommended by old-school security pro's.
In this week's edition:
🌐 Domain names to look out for👱♀️ SecPro turns Karen🔥 the quick and dirty
Reading time: 03:10
Domain names to look out for
Phishing is one of the most used security attacks.It's easy and, sadly, very effective.Often through e-mail and paired with domain spoofing, it's getting harder and harder to tell what is real and what is not.

A report published by whoisXML confirms this tactic is still on the rise. And with effect.
Here are some of the topics often used in domain spoofing;
Public trends. For example when Elon Musk was rumored to buy Twitter there was an enormous rise in domain being registered containing those terms. Bit weird, but it appears to work.
Global events. Like the war in Ukraine. Making use of the goodwill of people, a lot of domains containing 'Ukraine', 'support' and 'help' were registered and used to frame people.
Recurring events. Christmas, Black Friday, Valentines but also taxes and elections. Those are, if you ask me, the hardest ones.
I'm not sure what makes me lose more money though, clicking the real or the fake 'taxes due' mails..


SecPro turns Karen
Disclaimer: I own some crypto and 2 very unsuccessful NFT's, which I bought because they one is shiny and the other is a dancing potato.Nothing I say about crypto is to be taken serious.
Disclaimer 2: I hope nobody reading this named Karen takes offense. The internet decided Karen is the name we'll be using, I can't help it.
So, now that we got that out of the way. This article, by Ivan Kwiatkowski, I found at Kaspersky's site got my attention (a good title does a lot).One thing that's gotten very clear over the last few years is this:Whenever somebody is talking about crypto, they are either cryptobro's or cryptohaters. Not many people that talk about crypto and have a neutral opinion.And BOOOOOOY this guy is a hater.

He does a very good job at explaining the basic concepts though, and I'm quite a fan of the way he writes. Kudo's to that.So if you're curious about NFT's, DAO's and other crypto stuff, be sure to read part 1 as well.One thing did annoy me though, something which made it very hard for me not to write about it. So I did :DIt's this little part:
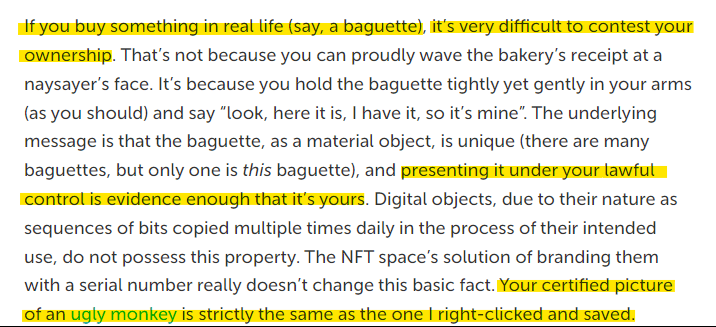
So by this logic, there's two things I want to address and then explain why this is just not true.
If I step into my neighbor's BMW and say "look, here it is, I have it, so it's mine", I'm now the proud owner of a BMW M3. I don't think I need to explain why this won't work, right? There is literally nothing which proves you own a baguette. Not even a receipt. The receipt proves you own 'a' baguette, not which one.
Two baguettes are not the same, but two digital pictures are. Why are two baguettes not the same? Different molecules. Why are two digital pictures (certainly when comparing a JPEG to an NFT) not the same? Different smart contract.


The quick and dirty
New NullMixer dropper infects your PC with a dozen malware families - gotto catch 'em all?
Critical WhatsApp Bugs Could Have Let Attackers Hack Devices Remotely - WhatsApp came with a quick fix, but this could have been a potentially dangerous situation.
Teen hacking suspect charged with computer misuse and breach of bail conditions - Investigation into GTA 6 and Uber data breaches continues. - ladies and gentlemen, we got him.
Meme of the week

Security like I'm five
Don't have time for hours of research? Don't have 20 years of experience in security? Me neither, but I gotchu fam.In Security like I'm five I cover a range of security topics. I do all the hard work, and explain it to you in a practical matter. Lot's of meme's too. Good stuff, good stuff.This and Security weekly conveniently delivered to your mailbox a couple of times a week, for free.Pretty sweet deal if you ask me.
So sign up for the newsletter and be enlightened! (don't set the bar too high tho)