- Disable User
- Posts
- Using Outlook? Update straight away! And some business tips for mature passwords.
Using Outlook? Update straight away! And some business tips for mature passwords.
Security weekly

Hi and welcome to another Security weekly. Where we laugh, we cry and share the latest and greatest in security and tech news.
In this week's edition:
📧 Using Outlook? Update straight away!
🔑 Follow-up: passwords
❔ Disable User Explains: Zero-Day vulnerability
🔥 the quick and dirty
Reading time: 03:13

Using Outlook? Update straight away!
Ok, stop. Freeze.

Before you start panicking, hear me out.
Microsoft latest ‘Patch Tuesday’ released 80 updates, including two zero-day vulnerabilities.
One of them is an exploit for everyone’s favorite mail-app: Outlook.
While the exploit is significant and the impact very - and I mean very - scary, you the scope is a bit.. unclear.
So, what’s so scary about this exploit then?
By altering an e-mail message, an unwanted intruder is able to steal your hashed credentials.
Okay, English?
Well. A hacker - in this case it’s our friends of Russian APT Fancy Bear - can alter an e-mail message into tricking your mail server to release your hashed credentials.
Mail servers often use NTLM - an authentication protocol.
Which is not unsafe by itself, but because it is old it has a lot of flaws, making it a target for hackers.
Ok, but it’s hashed, that’s safe, right?
Technically, sure. But you’d be surprised how easy it is to crack a password - I’ll explain further below.
It’s easy to find a database of hashes for common used passwords. Even on the ‘normal’ internet.
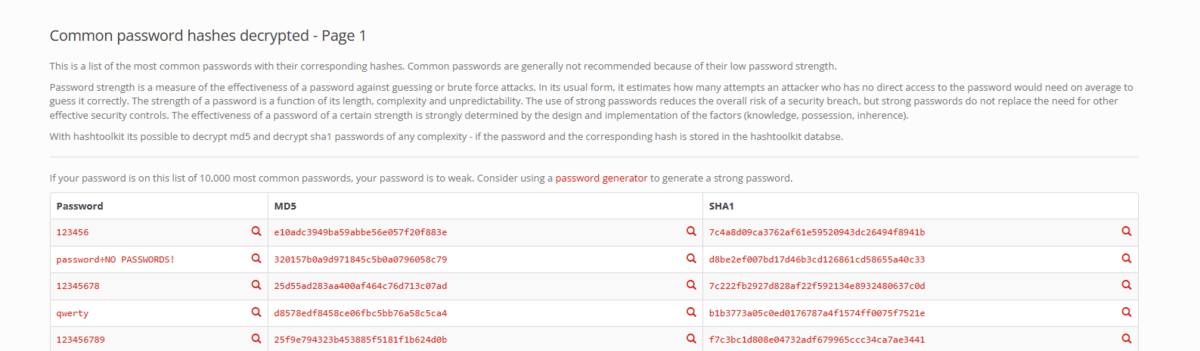
Literally the first hit in Bing.
So get some hashes, plug-in some computer-calculating-power and voila.
Cracked.
What confused me at first was the Scope of Microsoft’s CVE.
It says “All versions of Outlook”. So you’d expect .. all versions of Outlook, right?
They forgot to mention it’s all versions of Outlooks.. connected to Exchange Server.
So not Outlook on web, Exchange Online, …
Even after reading some articles I still couldn’t make up whether online was really “safe”.

Thanks for being so clear, Microsoft.
Still, with this severity and impact, I’d take no chances and update immediately.
There are some scenario’s in which Hybrid and Cloud environments are still affected, so I’d take no risk fix it straight away.
So without further ado, here’s what to do; (look at me ma, I’m rhyming)
Update Office to the latest build, check your build here - https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-23397
Well. That was easy. THANK GOD. We can all sit down, and down a brewski.

Why the Mortal Kombat you’re wondering? I have no clue.
If you’re an IT admin and want to see if your on-premise environment was breached, Microsoft provided a script via GitHub.

What does a good password (policy) make?
My claim earlier about “how easy it is to crack a password” might be a bit misleading.
It isn’t easy to crack a password.
At least not if you use a good, strong password. And not Summer2023.
Last week’s ‘Weak Password Report’ from SECOPS revealed ‘Password’ is still the number one used password.
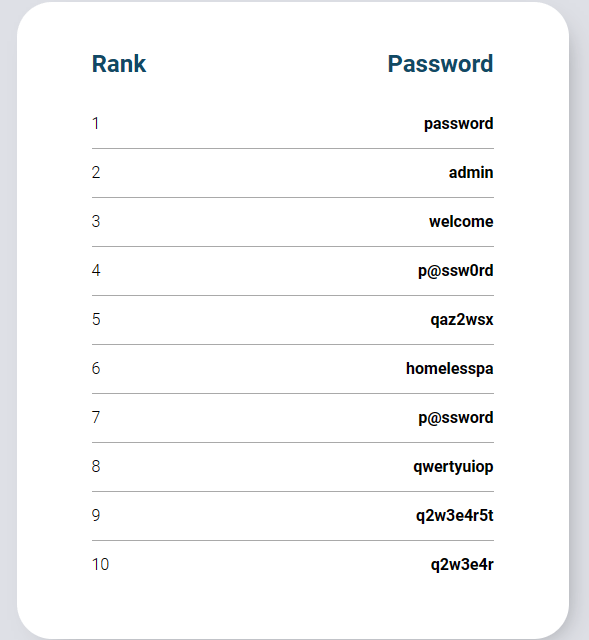
Real original, y’all.
So even with me ranting every week about week passwords, and every other (less important) cyber security media on the freaking planet screaming “PLEASE USE DIFFERENT AND LONG PASSWORDS”.
Even then, nothing changes.

So, here I am, once again, asking for your attention on this important subject.
But, you’re coming here to learn, right?
I made a promise I’d make things understandable, and practical.
So here are Ya boy’s 5 tips for better password management (personal and business):
Use a password manager - anything but LastPass
At least 12 characters, upper/lower case, numbers and symbols - speaks for itself
Change ‘em once a year - no more, no less. Unless you suspect faul play. Then change immediately
Don’t use words or phrases - dictionary attacks are often used, and make it way easier to crack your password
Don’t re-use passwords - Never.


Zero-day vulnerability
A flaw in a piece of software that is unknown to the vendor responsible for the application.
Unaware of this exploit in their software, this is either reported by bug hunters (lucky) or used by hackers (unlucky).
Once the flaw is known, the vendor releases a security update to patch it accompanied by a CVE.
Forgotten what a CVE is? In a dark past I wrote an article about it:


The quick and dirty
Microsoft SmartScreen Zero-Day Exploited to Deliver Magniber Ransomware - the other Zero-Day delivered this week.
AI-Created YouTube Videos Spread Around Malware - well if it ain’t those pesky AI robots again
Reddit is down in major outage blocking access to web, mobile apps - during this outage it was measured the internet contained 99% less nonsense.
meme of the week

Really curious if this worked.

