- Disable User
- Posts
- 🫰🏻 Why Windows Hello's fingerprint might not be as safe as you thought
🫰🏻 Why Windows Hello's fingerprint might not be as safe as you thought
But no, you're not being cloned

Hi and welcome to another Security weekly. Where we laugh, we cry and share the latest and greatest in security and tech news.
In this week's edition:
🫰🏻 Why Windows Hello's fingerprint might not be as safe as you thought
📰 Bits & Bytes
❓ Disable User explains: Cleartext
🔥 meme of the week
Reading time: 02:10

Last week in Cybersec
Upheaval around iOS 17's NameDrop Feature
US Law enforcement agencies are warning about iOS 17's NameDrop, suggesting it could share your contact info with nearby iPhone users.
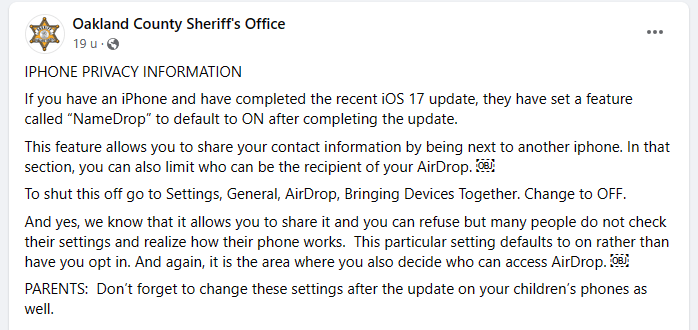
Solid Facebook advise.
iOS’ NameDrop is like accidentally broadcasting your number at a crowded bar, but only if your phones are practically kissing.
It requires physical closeness (phones touching tops) and a mutual decision to share or receive contact details.

The fear might be overblown. To share info, iPhones need to be extremely close, and you control what's on your Contact Card.
An accidental share?
Just separate the phones or lock yours.
Apple's advice: "To cancel, move the two devices away from each other or lock your iPhone."
Overall, not bad advise. But I’d be careful with anything I read on Facebook.
Windows Hello Fingerprint’nt
Security holes in Windows Hello's fingerprint authentication have been uncovered on Dell, Lenovo, and Microsoft laptops.
Well, they haven’t tested it on others, so that might be a bit misleadingly worded.
Researchers found ways to bypass this security feature, raising both eyebrows and concerns.
The vulnerability lies in the "match on chip" fingerprint sensors.
These sensors are meant to be secure, storing biometric data on a separate chip. However, researchers managed to mimic these sensors, tricking the laptops into thinking an authorized user was logging in.
The flaw isn't in the Windows Hello system itself but how manufacturers like Dell, Lenovo, and Microsoft implement it.
Some bypassed Secure Device Connection Protocol (SDCP), meant to store the info safely, while others transmitted security data in cleartext or used flawed security protocols.
I never liked the fingerprint option, but that’s pure lazyness. I do love it when my lazyness pays off though.
On a real note, as with much of these findings: the likelihood of this happening is very small. But it doesn’t hurt to validate how your device handles this info.
Storing stuff in cleartext is just… poor practice.

Can’t be bothered looking it up? Just Disable it: Go to [Sign-in options] in Windows, find [Fingerprint recognition (Windows Hello)], click [Remove], and voila.
Ps: it was Dell who did cleartext.

Bits & Bytes
Citrix Bleed widely exploited, warn government agencies - Act surprised, it’s a Citrix bleed.
Malware dev says they can revive expired Google auth cookies - oh c’mon. This is why we can’t have nice things.
Microsoft: Lazarus hackers breach CyberLink in supply chain attack - Didn’t know CyberLink still existed. This takes me back..
AI Solutions Are the New Shadow IT - Don’t dump sensitive info in any AI tool please. Make my life a bit easier. Thanks in advance, regards, ya boy.
ClearFake Campaign Expands to Target Mac Systems with Atomic Stealer - Updates don’t come through ads. Always download them through the OS/App store. Be mindful!

Cleartext (plaintext)
Data transmitted or stored unencrypted, making it easily readable without any decryption.
Like shouting your password in a crowded room and hoping everyone's wearing headphones.


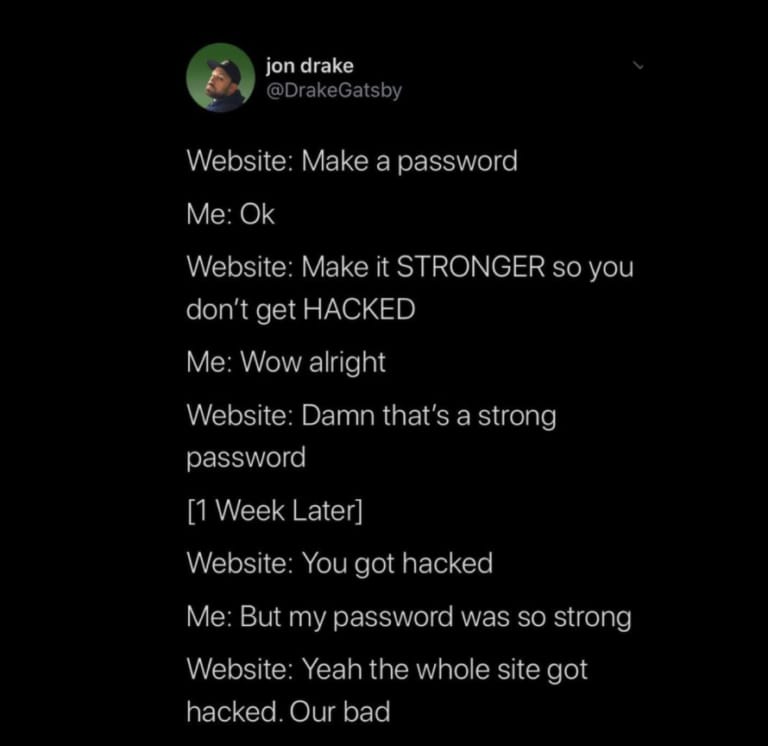
Meme of the week