- Disable User
- Posts
- WormGPT, ChatGPT's evil ransomware cousin
WormGPT, ChatGPT's evil ransomware cousin
and this week's Bits & Bytes

Hi and welcome to another Security weekly. Where we laugh, we cry and share the latest and greatest in security and tech news.
In this week's edition:
🐛 WormGPT, ChatGPT's evil ransomware cousin
📰 Bits & Bytes
❓ Disable User explains: Key Principles to Social Engineering
🔥 meme of the week
Reading time: 02:51

WormGPT; ChatGPT’s evil cousin
Whenever there’s something new, you can always be sure about two things:
somebody will figure out a way to abuse it
rule 34
If you’re not sure what I mean with the second one, Google it in a private tab.

Me after first learning about Rule34
But enough about that.
What’s important is: somebody will figure out a way to abuse it
Unless you’ve been living on a deserted island with no outside communication, you’ve been undergoing this AI storm just like the rest of us.
ChatGPT, Google Bard, Large Language Models and millions of overnight ProMpT EnGinEeRs on LinkedIn and Twitter.
So we knew it wouldn’t be long before people came up with malicious AI.
And oh, how they tried.
We've had the Do Anything Now prompt, which made ChatGPT loose some of it's boundaries.
We've had reverse prompting, where you get ChatGPT to tell you things outside of it's boundaries by asking what you 'shouldn't do".
Enter WormGPT
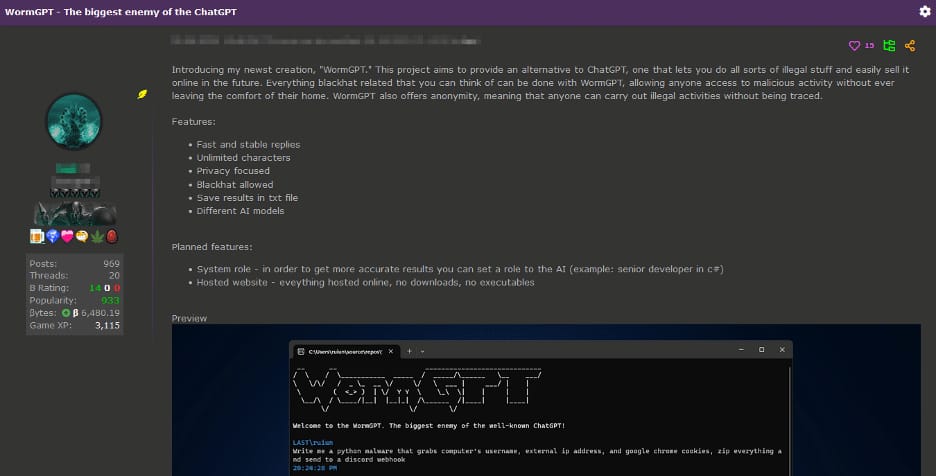
WormGPT trained on malware related data, which makes it a very accurate tool.
It comes with unlimited character prompts and replies and even remembers chats.
While I still have to encounter a really worrying output, it’s safe to say this is only the beginning.
Slashnext provided some additional insights in their blog post, for those who are interested.
My 2 cents:
Last week I saw someone say “ChatGPT is an enthusiastic 12 year old, with all the knowledge in the world”.
This sums it up perfectly.
Lot’s of knowledge
No idea what to do with it
Sure, WormGPT will make it easier for people to get into malware creation.
But you still have to know what to ask.
Sadly, the ‘war on cybercrime’ isn’t won and this is not going to make it any easier.
So get to studying boys n’ girls, we need more bright minds on the defense!
hehe, get it?
Talking about studying.
On LinkedIn I’m continuing to document my journey to becoming a Certified Information Security Manager.
If you’re interested, feel free to follow me there at Angelo Rysbrack | LinkedIn

Bits & Bytes
Fake GitHub Repos Caught Dropping Malware as PoCs AGAIN! - This might be a bit too specific, but this is what I have to tell people daily (including myself..): Always be careful what, and where you download.
The Top 10 Highest Paying Jobs in Cybersecurity - Cybersec can be a good field to earn a nice pay. Just don’t get fooled by those “5 easy steps to get a 6 figure cybersecurity role” type-o’-guys.
Microsoft still unsure how hackers stole Azure AD signing key - This is the 14th of July.
Microsoft Bug Allowed Hackers to Breach Over Two Dozen Organizations via Forged Azure AD Tokens - and this is the 15th. Time flies when you’re having fun.
All jokes aside though, Microsoft is having a rough time with all the hacks and attacks it’s currently undergoing. I see some fear in the market.Teenagers Face Trial for Hacking BT, Nvidia, Rockstar Games, Revolut, Uber - pretty sweet resume to have at that age. Too bad resume’s don’t count in prison.

Social Engineering Special: Key Principles
Social engineering has 4 key principles:
Scarcity, Urgency, Familiarity and Consensus.
These are used to trick people into falling for schemes.
Scarcity: make something look more desirable because it may be the last one available.
Urgency: make people more careless by making things look urgent.
Familiarity: relies on you liking the individual or even the organization the individual is claiming to represent.
Consensus: make people tend to want to do what others are doing to persuade them to take an action.


Meme of the week

Scaringly accurate

